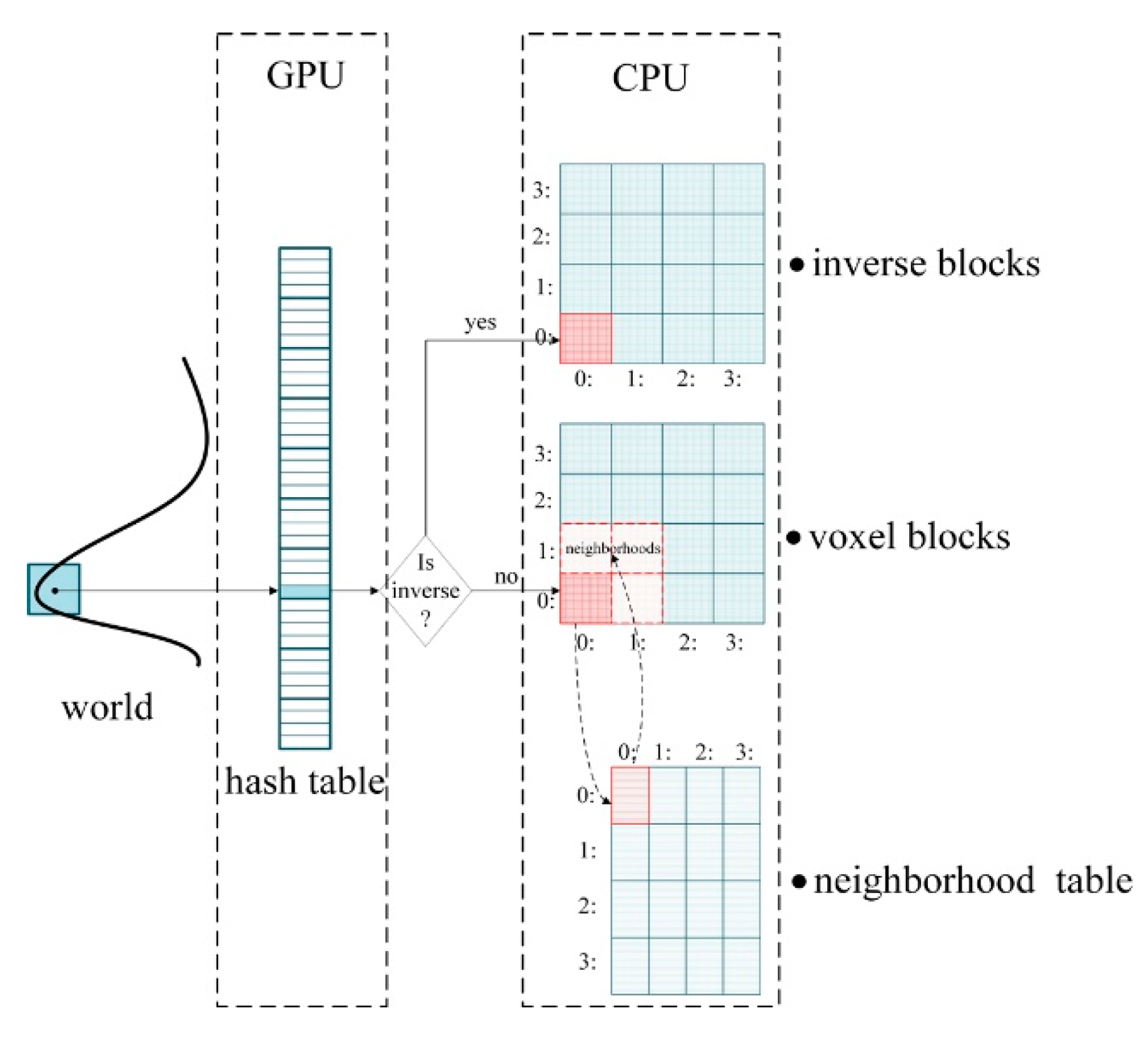
Sensors | Free Full-Text | Real-Time 3D Reconstruction of Thin Surface Based on Laser Line Scanner | HTML
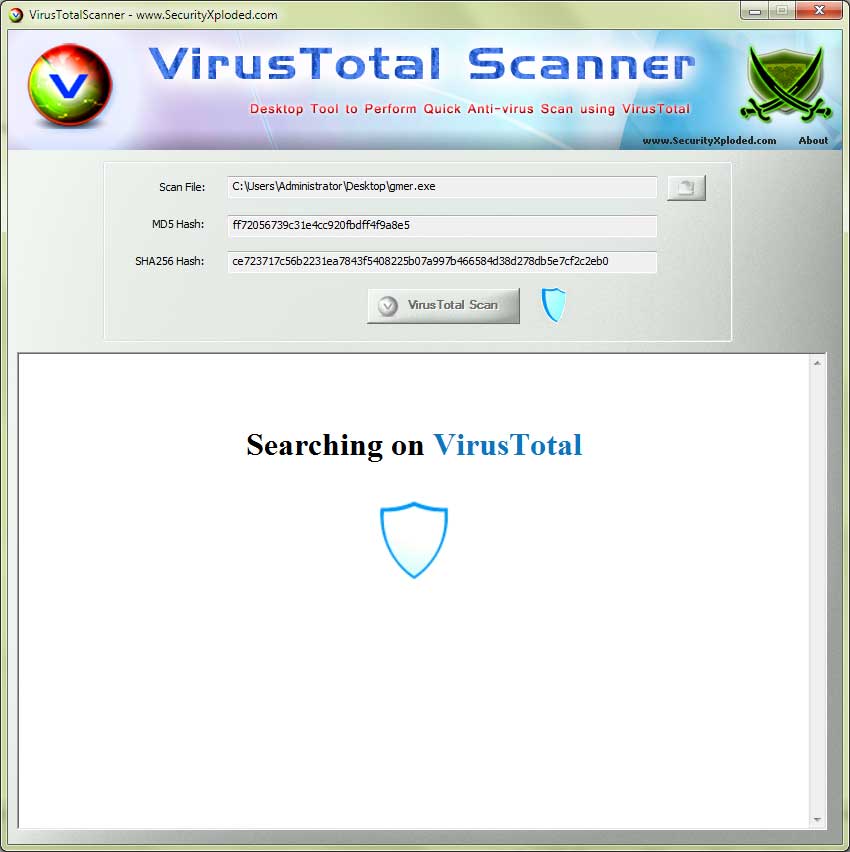
GitHub - sceptreone/Virus-Total-Mass-Hash-Scanner: Single Page site which helps scanning multiple hashes using limited API keys from VirusTotal.